If dealing with COVID-19 and 100% remote workforce is not enough, businesses of all sizes and in all verticals are facing an exponentially more frequent and more sophisticated siege of cyberattacks. However, for those small to mid-market businesses (SMBs), there is likely worse news. Bad actors/hackers/hacktivists/cybercriminals are targeting them specifically since there is a well-known weakness. Most SMB organizations aren’t as well prepared to defend and respond. https://www.bizjournals.com/sanfrancisco/news/2020/09/28/hacks-of-fortune-500-business-may-make-the-headl.html
Part of the reason for this weakness is that many SMB organizations don’t understand that cybersecurity is a multi-phased, continuous program, not a “once and done” effort. Cybersecurity is the fifth dimension of warfare. You and your organization are in this war, whether you like it or not! All too many think that if they buy and deploy the right security widget or outsource it all to the right support service provider, they are good-to-go. Nothing could be further from reality, and such misconceptions have never been more dangerous to their organization’s livelihoods. Depending on where your organization is on the maturation of your program, you can enter that lifecycle at any point within it.
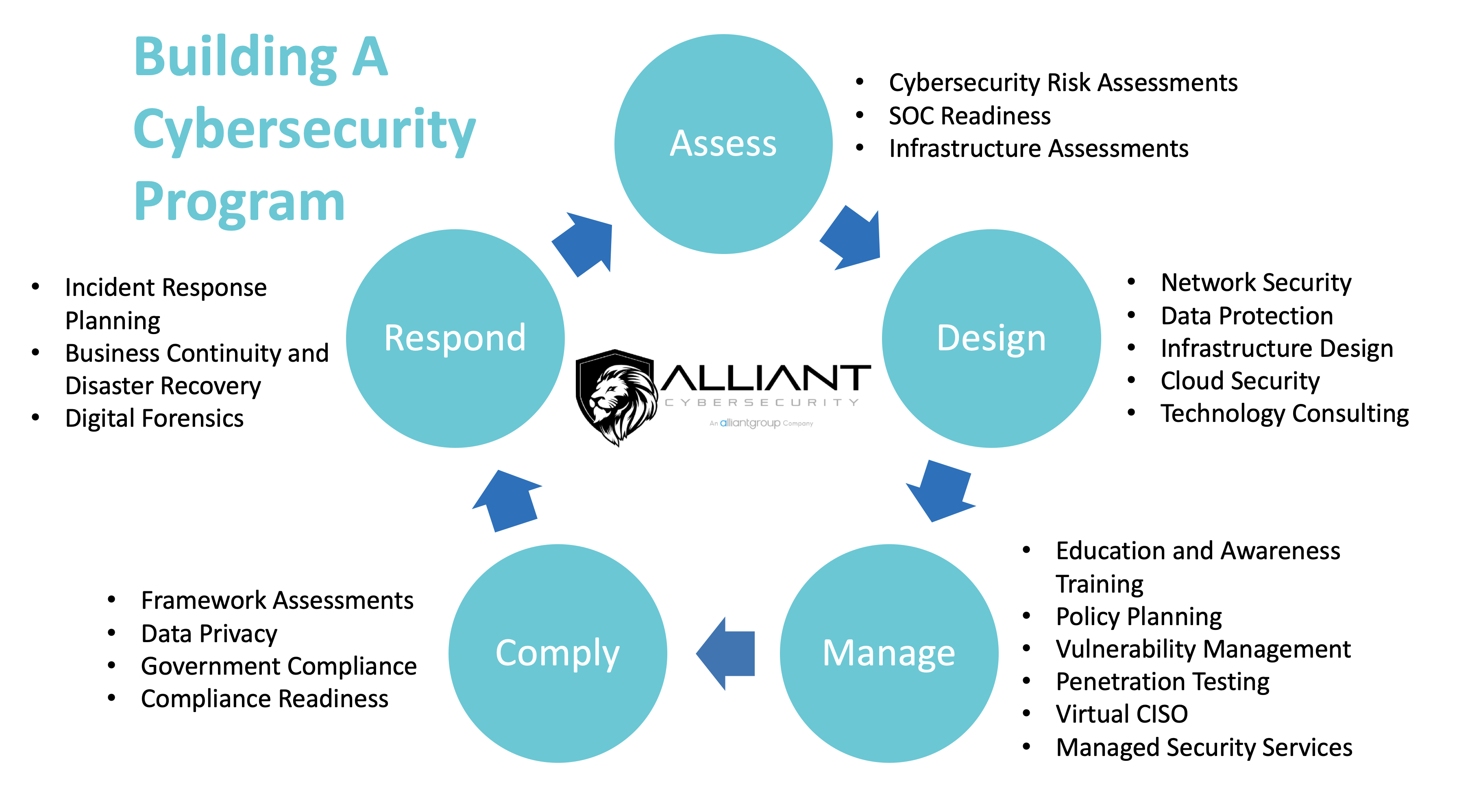
In this series, we will help you understand each phase. We will share where, ideally, you should enter the program and how to make continuous incremental improvements – all without breaking the bank. Let’s begin with ASSESS.
Just as many people take their car in for annual inspection, or as individuals, we should get annual health checkups, so should all organizations take stock of where they are now, and what gaps exist in a roadmap for continuous improvements in data privacy and cybersecurity. Note the use of the word continuous in the preceding sentence. As technology evolves, so will the bad actors and new threats. New features will become flaws ripe for exploitation, and data privacy legislation will evolve, so too your defenses have to continuously improve. The word, Roadmap is also apropos as well. After all, if you do not know where you are or where you need to be (i.e. no map), any road will definitely get you lost! Assessments, a little different than audits, should follow a well-established framework and appropriate legislation relative to your industry like the FTC Safeguards Rule, CIS Top 20, NIST, ISO, CMMC, etc. These examinations should be holistic, covering not only technology (Security is NOT just an IT challenge), but also if you have the right people, trained, and following the right processes and controls for data privacy and cybersecurity. Assessments should be performed at least annually and more often as business changes warrant (e.g., mergers, divestitures, new lines of business, going to or from the Cloud, other major tech changes, or to or from majority remote workforce, etc.). They should result in risk ranked list of finding and recommended solutions based on the likelihood of occurrence and impact
Assessments are the first step in every recognized best practice and framework world-wide. If your business is part of the supply chain in heavily regulated industries or a provider of services/products to governmental entity supply chains, there are likely laws that require you to perform these assessments at least annually as well. The bottom line is they are not a nice-to-have, but a must have. They can be performed by your own internal staff if they are qualified and will be objective. Playing fast and loose, wink-wink, with risk rankings is a good way to end up worse than before you undertook the assessment.
The cost of the assessment by a qualified, objective, outside, advisory services provider will be a tiny fraction of the cost of what responding to an incident will cost. The assessment will let you know what risks should be addressed in what order. The best of them, like those supplied by Alliant Cybersecurity, provide actionable insight on how to pragmatically improve your cybersecurity and data privacy posture in short order. This alone lowers your chances of being compromised.
Our next installment will address data privacy and cybersecurity by design. See you then. In the meantime, BE AWARE. BE SECURE.
Ransomware is radically increasing just in time to destroy everyone’s confidence in election results:
https://www.nytimes.com/2020/09/27/technology/2020-election-security-threats.html
9-1-1 services in multiple states hacked:
https://www.dailymail.co.uk/news/article-8783411/911-services-suffer-nationwide-outage-officials-race-restore-emergency-lines.html
An entire chain of hospitals forced to revert to paper patient medical records: https://abcnews.go.com/Business/wireStory/cyberattack-hobbles-major-usuk-hospital-chain-73300013



